Definition: Two factor authentication is using one extra form of authentication along with the basic authentication method. For eg. Very basic verification method is, using a password; along with this, we add another passcode or PIN to gain access.
Here in this post, we will discuss
- Multi Factor authentication
- Two factor authentication: Do we really need it?
- Two factor authentication: why it is neglected?
Today’s modern life where most of the peoples’ personal or work life is digitalized and the latest technology provides access to your data easily almost at all times and anywhere. Any data like your personal photos, bank account details, your working project files, location of your car, kids even your pets. Sitting at one place we could operate and access our data. As we are getting the comfort of these technologies there is always a risk attached to it.
Yes, the data is available but the question arises is the availability only to the owner or to whom it has to accessible? Or is it also available to any other unauthorized user?
With the increasing convenience over the internet in the availability of the data, we are adding more and more data to the internet world. Both the personal and professional data that we need, we save them over the internet. With in the organization, the top most data which is a high priority to save are the details related to their customers and the personal data which is highly risky losing over the internet is their identity.
Many other data related to personal are saved over the internet which should not be accessed to any other unauthorized user like their Physical locations(GPS), their credit history, bank account and payment details, telephone numbers, and even the health conditions which have to be secured.
Similarly, in the working environment the data related to the business like their business secrets, customer information, marketing strategies and the sales they made, research and development details.
These data if lost could incur huge losses to the businesses or the personal lives and thus they need to protect them, secure them on top of without losing the availability of the data.

Daily the IT industry is trying to improve the security to protect these data stored online, and the hackers on the other side improving and inventing new methods to breach the security the most common types of risk and attacks we see over the internet are Phishing emails, Man-in-the-middle attack, credential theft.
So, these attacks increase the awareness in the users to use the strong mode of security to secure their data, this could be achieved using the strong passwords and yet which is proven not a fully secure way to achieve the goal.
Most of the time, poor handling of the passwords by the users provides an easy spot for the hackers to breach the security and access the data. Common types of practice like writing the passwords manually on the paper or on to the sticky notes which are very easily accessible by anyone. Saving the password in excel sheets or word documents without proper protection.
Due to ease of usage, most of us save the passwords on the browsers which will make possible loophole for the intruders to gain access.
Before implementing a second layer of authentication we first need to secure the first level or the basic level of password habits which will secure the data at the very basic level. So, for this what we can do to protect or passwords
- Use random letters and numbers combination chosen passwords
- Refrain from using the same passwords
- Set a minimum password length 10-12 digits
- Change your password periodically
Instead of choosing a simple password or passwords with common names, words or guessable phrases creates a poor password, so we should start using the password with random letters and number which will be difficult to guess at the very basic level. Increase the length of the password required will create little extra security than the shorter passwords. Change your passwords periodically this will give an added advantage if someone trying to guess your password will be left behind. Do not use the same passwords on different accounts or when you change your password do not use the old passwords.
As today’s computing power has increased creating brute force (method to generate series of passwords) attack with the much-increased combination is made possible and they can create millions of possible combinations even up to 10 digits very less time and a complex password can also be cracked by the hackers. To barge this we need to add an extra level of authentication which will make it difficult for the hackers to gain access even if they succeed in breaking the complex password.
Adding a firewall or antivirus provides an extra security feature to avoid phishing emails and other forms of spam emails where the possibility of leaking the passwords.
Multi Factor authentication
So let’s see what is two-factor authentication briefly like in the beginning, we said it is a method where we add an extra verification process required to gain the access. In general, we can use a combination of different types of verification along with the basic level of verification.
We can define them in 3 different groups like
Group 1: Things that we have:
Here we can group the things which we have and can be used as proof of identification like our smartphones, flash drives, keys or even the special token generation devices.
Group 2: Things that we know
Something that we can remember and only we know like another password, PINs, passcodes or security questions that only you know the answers. This option we can use even for the recovery of the access.
Group 3: Things that we have
Using modern technology we can use our body parts as a mode of verification like face recognition, fingerprints, retina scan, voice recognition.
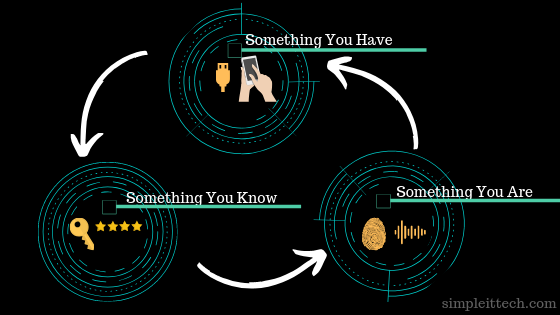
Using any combination of these 3 groups we can create a two factor authentication method to provide an extra layer of security.
Two factor authentication: Do we really need it?
Now we have seen the use of two factor authentication but still, the question comes to us why we need this two-level of authentication.
To better understand the need of the second layer of authentication let me take you to the story of

“Ali Baba and the forty thieves”.
Most of us heard this story in our childhood or in some part of our life that how Ali Baba overheard the secret voice command(“Open Sesame Open ”) from the thieves to open the rock of the cave to enter where he was easily able to take the gold as much as he can and close the door.
The point here to bring this story is that what if the thieves had a second level of authentication along with the famous voice command
(pinch the horse’s ear or handprint of the head of the thieves. Eh! PJ 😉 )
then it would be difficult or next to impossible for Ali baba to open the door just by the voice command what he heard it from them.
This is just to bring the importance of having an extra feature where the proof of identification is coming from the owner itself.
If we have the only password to protect then for the intruder has to attack to break the single mode of authentication to gain access and if there is two factor authentication then he has to wage multiple successful attacks on both methods to break through which usually very difficult to achieve.
Knowing the importance of two factor authentication most of the online services implement this feature, for example, the banking sector sends SMS codes to the registered mobile phones or use a device to generate a PIN to log in or while doing any transaction along with the usual login credentials.
Two factor authentication: why it is neglected?
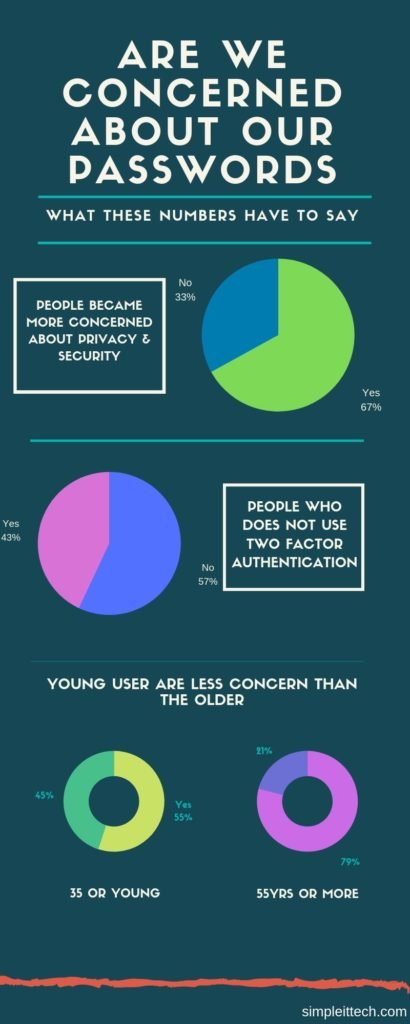
As per the recent research by Ponemon Institute it shows that around 67% of people have become more concerned about securing the password yet 57% of people have not changed the behavior of the password used. That means there was no two factor authentication implemented.
Most common reasons for not using the two factor authentication can be listed out as
- It is not easy to manage the passwords
- Extra wait time during the logon or transaction
- Fear of losing the device used for the second level of authentication.
- Not easy to remember the security bypass codes for the recovery process
Most of us feel like it is very difficult to manage the different passwords while maintaining the complexity in the passwords. Along with this it generally takes time when we use 2nd level of authentication either by SMS or token generation device where we have to wait for the SMS to arrive to the telephone or for the PIN to be generated by the device.
We even think what if we lose the device to authenticate let’s say we use our smartphones to get the second level authentication by using a mobile authenticator app that has lost. Then how is it possible to login without the phone then we should have the recovery process or bypass method to use another form of authentication. Even the recovery codes which are used to bypass or use as an alternate method to authenticate are not easy to remember and lead to poor handling of the data.
So these few things are keeping most of the users away from using the two factor authentication in most of the places unless it is been imposed as a compulsory method of verification.
Examples of Multi or 2 factor authentication
- Gmail authenticator app
- Apple ID two authenticator app
- Instagram authenticator app
- Microsoft multifactor authentication
- Twitch 2fa
- Paypal two factor authentication
- Outlook 2-factor authentication
- Netflix two factor authentication
And most of the many other application uses two-factor authentication.
Conclusion:
After this, we can conclude that yes, there is a need for two factor authentication but there is also a need to create a process where users can login without any passwords. Until then it is us to decide depending on the level of security needed by the data either to implement the extra level of authentication or not.



